3 Important Security Aspects of Card on File for Your Medical Practice

Making a payment online with your doctor should be a seamless and secure transaction. Adding a card on file for future transactions should likewise be the same. Keeping your card on file makes future transactions easier and saves you the time and trouble of realizing you forgot your card at home while in the waiting room, or the hassle of fumbling for your card while on the phone with the doctor’s office. In today’s world, a card on file is honestly the next evolution in making a payment, and it should be simple, trusted, and secure.
But the headlines can scare us. In 2014, the information from 56 million credit cards was stolen from The Home Depot. In 2006, 94 million cards were hacked from TJX companies, including the TJMaxx and Marshall’s retailers. And in 2009, 160 million cards were stolen from Heartland Systems. These hacks might appear to be “old news”, but as we’re still recovering from the big Equifax breach of 2017 which affected 143 million of us, Capital One announced in July of 2019 that 106 million credit card applications were hacked, including social security numbers and bank account information.
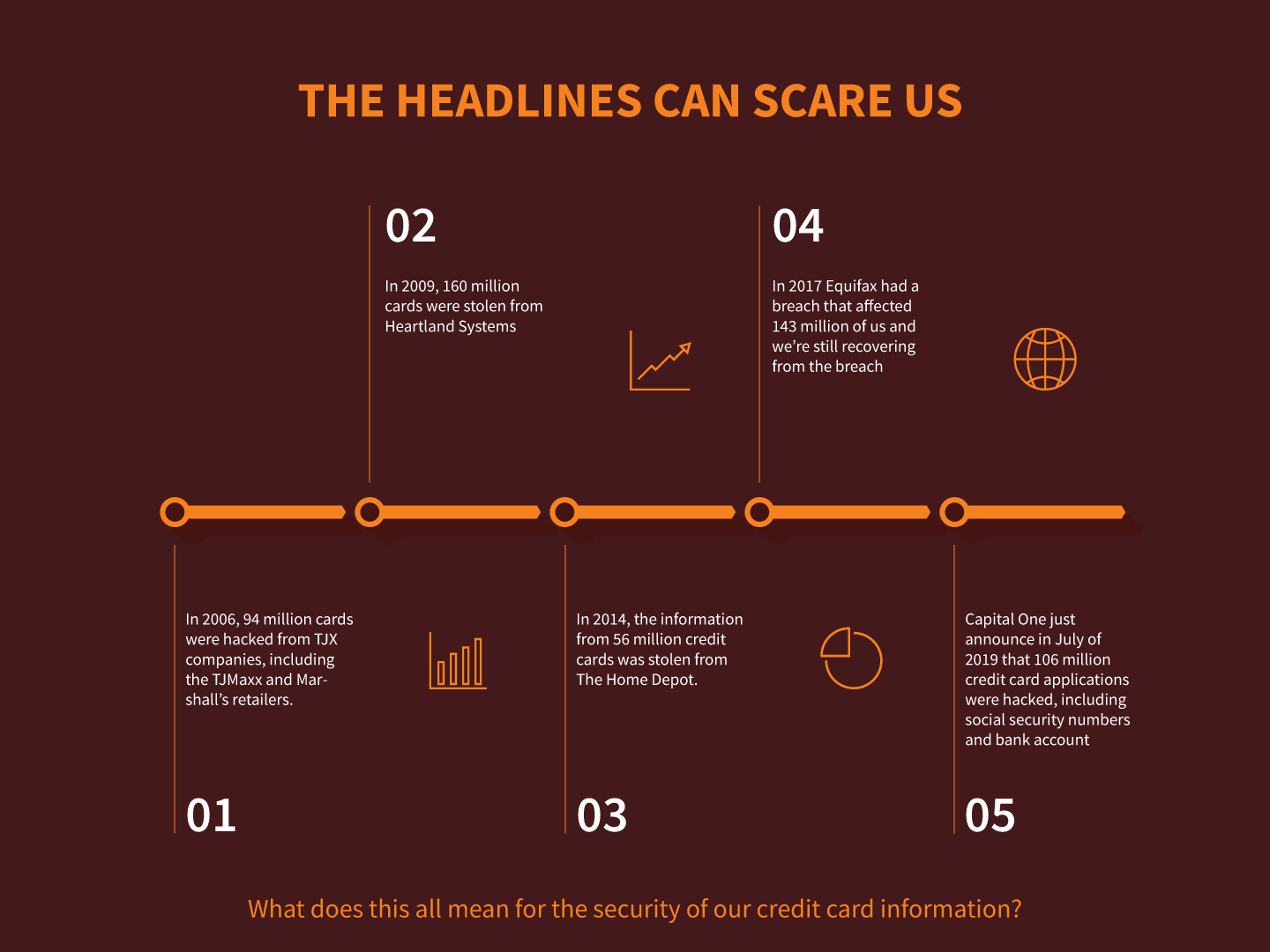
What does this all mean for the security of our credit card information? Is the safest place for our credit card still our wallet, or can we trust that vendors will keep our information secure? Storing a card on file means that somebody somewhere has it. And what happens if it gets hacked?
100% Secure
The Payment Card Industry Data Security Standard was developed in 2006 by Visa, Mastercard, American Express, and Discover to help regulate the credit card industry and manage payment standards in an effort to improve payment security throughout the industry. The breaches just mentioned occurred primarily because these standards were not in practice, or not practiced very well. When our information security is concerned, a passing mark for PCI Compliance is 100% and nothing less.
Security comes from tried-and-true best practices. In the payments industry, PCI DSS was developed as just that. PCI DSS Compliance is defined by 12 requirements, including; encryption of transmitted card information across public networks (like the Internet), restriction of physical access to cardholder data, and the establishment of secure policies governing the protection of data, just to name a few. The bad news is that PCI Compliance is not required by federal law. To make things easier, there is a PCI DSS Certification that companies can undergo to demonstrate their compliance. Another certification that encompasses PCI and many other medical-related areas is the HITRUST Certification. The rigorous controls put in place through this certification process not only demonstrate and prove a business is PCI Compliant, but also HIPAA Compliant and also compliant in many security standards including ISO, COBIT, and NIST. An organization that is HITRUST Certified has demonstrated their adherence to best practices and puts security and protection of data at the forefront of their business model.
As a rule of thumb, look for these certifications with your payment vendor, or if you’re a patient, ask your doctor’s office about them. Peace of mind for a medical practice, or for you as a patient is of great importance when allowing your card to remain on file at a business. Ask the questions and know that they are compliant and secure before allowing your information to leave your wallet!

Use a Trusted Vendor
Trust is hard to earn and easy to lose. Again, we circle back to best practices. These demonstrate our actions and resonate louder than words. Is our payments vendor trustworthy in their actions and their practices? Do they use secure protocols to accept payments, such as the https:// in their web address? In what ways have they demonstrated trust with your medical practice and what measures have they taken to remain secure?
Storing a card on file needs to follow two important rules; one, the data is being encrypted, and two, tokenization technology is being utilized. Encryption is a definitive way around the prying eyes of a hacker. And the practice of storing encrypted data in one location, and the decryption key in a second location is very important. What could be worse than a hacker gaining access to your systems and discovering your stored and encrypted credit card data, and then finding the decryption key sitting right next to it! Separating the two adds a level of security and demonstrates trust by the vendor.
Most card on file solutions allow for the sensitive card storage to be done at the merchant. This comes in the form of tokenization. Essentially, a credit card’s information is securely transmitted to the merchant and they return a token. A token is a number generated by an algorithm that is assigned to a patient’s card on file. When payment requests are submitted for a patient’s card on file, the actual credit card information is never exchanged, just this token. And this token, if it were to be compromised, is useless. It contains no actual credit card information. If a hacker were to snoop on the credit card transaction in cyberspace, they would basically hear the following digital conversation: “Doctors Office: I need to make a $50 payment using John Doe’s Visa. Merchant: Okay, we will process that payment for you using John Doe’s Visa. The payment was successful, here is the receipt.” And that is all. No exchange of confidential information and no exposure of sensitive credit card data. Tokenization is the most trusted way to make payments.
A Simple Process
Your payment solution shouldn’t have large overhead or any cumbersome processes. It needs to be fast, efficient, and most importantly, simple. People are busy, especially your patients. They took time off work, came into your office, and need to get back on the road. Being able to commit a credit card transaction with their card on file should literally take seconds, whether in the office or over the phone. Adding simplicity to the payment process will allow you to focus on your patients while providing them with the peace of mind that their credit card data is secure.
When security is considered along with industry best practices, a solution that is easy to use should be the outcome. Simplicity is not always simple. But when all the right building blocks have been used beforehand, it should be the outcome. Make sure your payments vendor is employing security best practices, and that they are a trusted partner. These two ingredients make up the recipe for a simplified process that can ensure your card on file transactions are being done right!
Out of the Wallet and into the Cloud

When you see a vendor with PCI or HITRUST Certification, and when you see them demonstrate trusted practices, then you know that your payments vendor has done their due diligence and is providing you and your patients with a secure, trusted, and simple process for facilitating payments with a card on file. Our private information, including our credit card information, deserves to be secure and protected by the places we do business with. It should be as safe with them in the cloud as it is in our wallet. Adding card on file to your medical practice will help generate revenue and ensure a higher percentage of payments are being made. Asking the right questions and doing your homework on your payment vendor can help you confirm that they are secure, trusted, and are providing your medical practice with a simple solution to facilitate card on file payments. Then you can focus on what you do best, which is taking care of patients!
Final Thoughts
Working with third-party service providers that perform a variety of functions, such as handling patient statements and patient payments, helps you navigate the increasing cost and complexity of running a healthcare practice, allowing you to improve cost-efficiency, augment the patient experience, and boost your bottom line.
To safeguard your patients’ interest while ensuring that your organization stays compliant to avoid hefty penalties and protect your reputation, you need to select vendors that are HITRUST-certified so you can rest assured that your patients’ sensitive information is in good hands.
LEARN MORE ABOUT HOW OUR SOLUTIONS CAN SAVE YOU TIME AND MONEY!
![]()



