Critical Healthcare Cybersecurity Measures to Protect Patients

As the healthcare landscape undergoes a rapid digital transformation, safeguarding patient health information (PHI) and ensuring robust healthcare cybersecurity have become paramount. However, traditional cybersecurity practices may no longer suffice in today’s evolving threat landscape. Fortunately, various cost-effective strategies can be implemented to maximize data protection and minimize vulnerabilities, even with resource constraints.
Recent research suggests ransomware attacks on healthcare institutions have doubled within the last five years, further highlighting the industry’s susceptibility. These concerning statistics underscore the urgent need for healthcare providers to adopt effective cybersecurity measures. The following tips can assist in safeguarding sensitive patient data and ensuring your practice is cyber-resilient.

2 – Factor Authentication
Unfortunately, a simple email or username and password combination is no longer enough to prevent hackers from accessing your information. In addition to hacking tactics becoming more sophisticated and cloud data being easier to access from anywhere in the world than data stored on hard drives, a shocking 83% of people surveyed in a 2018 study reported using the same password for multiple sites. This means that if a hacker obtains your login information from a relatively harmless site, such as an e-commerce website or a social media account you no longer use, the hacker can then easily access more sensitive data through portals like a bank account or a work login.
Because of this, employees who work for healthcare organizations are a liability to the organization itself. One way to combat this cybersecurity risk is to implement two-factor authentication into all employee log-in portals. Rather than simply logging on to a secure platform with a username and password, 2-factor authentication then asks employees to verify themselves before accessing the portal. Some commonly used 2FA features are requiring the user to answer security questions or a PIN number, or requiring the user to enter a code that the portal has sent to their cell phone number or email linked to their account.
Update Your Software
It’s no secret that hospitals and healthcare organizations have a tendency to rely on old and outdated software for far longer than they should. But beyond causing slow computers and a layout that is no longer user-friendly, outdated healthcare software also poses a massive risk to your organization’s cybersecurity. Old iterations of software such as Internet Explorer will stop receiving security updates as new versions are released, meaning they become weaker (and slower) over time.
The first step to solid healthcare cybersecurity is to initiate a conversation with your software provider about how to update to the most secure version of their programs without going over budget. Remember, however expensive upgrading your security software is, a data breach will undoubtedly be even more costly for your both company and your patients. And, while your employees might only begrudgingly transition to this new software at first, they’ll soon be thankful when they’ve realized their computers work faster with easier-to-use, more modern applications.
Employee Training
While two-factor authentication and up-to-date software are important, your employees are the last line of defense between your healthcare organization and a data breach that will cost your practice potentially millions in employee work hours, legal fees, and fines. Unfortunately, without training, this line of defense doesn’t work that well; in the first half of 2019, 60 percent of data breaches were the result of internal human error. Of course, not all of these internal data breaches were the direct result of a negligent employee, but the lesson here should be that technology alone won’t protect your medical practice.
To prevent a data breach caused by a well-meaning but forgetful employee, work with your practices’ IT department to develop and administer an annual or bi-annual cybersecurity training. Use case studies, real-life scenarios, and multimedia presentation formats to deliver the presentation in such a way that helps employees remember key takeaways.
Selecting topics to include in employee training should be up to you and your IT team. Be sure to go over any new security software, as well as some easy tips to prevent hackers, including:
- Not using public wifi to do work-related tasks without first connecting to a VPN
- Being wary of letting people you don’t know use your work computer, or of letting strangers into the building where you work
- Not clicking on any links or attachments from suspicious or unexpected emails (and how to identify which emails are suspicious)
A four-hour training will likely oversaturate your employees with irrelevant or niche information, but a half-hour to an hour presentation about the role they play in data breaches will help them retain information and more actively defend against data theft.
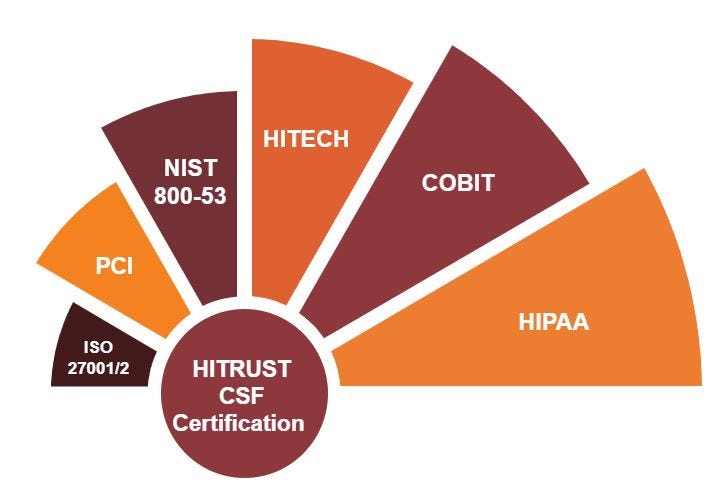
Make Sure Your Vendors are HITRUST Certified
Third-party vendors, especially for administrative services such as mailing and billing, are tasked with delivering sensitive information to the correct recipients several thousand times per month. PHI, insurance and credit card information and even the most basic information like names and emails are routinely transferred from healthcare organizations to these vendors, and therefore an ideal target for hackers looking for weaknesses in your organization’s defenses.
Unfortunately, even though the relationship between your medical practice and your billing service is purely professional, a data breach from within the company will impact your organization just as severely as if the data breach came from you (especially in the eye of the public). So, in addition to spending time ensuring that your own organization has a strong cybersecurity framework from your software to your employees, make sure your vendors also operate with data theft prevention in mind.
One feature to look for in current and prospective vendors is HITRUST certification. A HITRUST certification means that an organization follows HIPAA security compliance standards, and is a standardized approach for healthcare organizations to mitigate security risks. Beyond HIPAA, HITRUST certification also means that vendors are up-to-date on other security regulations in the public and private sector including HITECH, PCI, COBIT, NIST, and FTC.
HITRUST certification takes place every two years and closely analyzes an organization’s IT security practices and risks. By staying well-versed in such a wide variety of healthcare cybersecurity measures, HITRUST-certified vendors are better equipped to prevent data breaches before they occur.
Learn More: 9 Ways HITRUST Helps Healthcare Providers Protect Patient Information
MailMyStatements was one of the first medical billing vendors to earn a HITRUST Certification in 2016; to learn more about how MailMyStatements handles sensitive PHI and billing information, click here.
![]()